ABC Logistics Ltd specialises in temperature-controlled food warehousing and deliveries. It operates a fleet of 150 trucks from its four regional depots. ABC subscribes to a market leading software package, XYZ Cargo, that helps the company to remotely monitor and manage the refrigeration units attached to each truck, including cargo temperatures, maintenance scheduling and location data via an ‘always on’ wireless telemetry feed constantly streaming from each refrigeration unit. The data sits in the cloud, managed by XYZ, and can be accessed 24/7 by the ABC operations team.
Lily Jones works in ABC’s operations team, collating regular reports on cargo temperatures and other metrics for her boss. Lily accesses the telemetry software via the software vendor’s portal and uses her username and password to access the data. To keep things simple, she uses the same password across her favourite social media accounts.
Stage 1
A hacker buys Lily’s stolen social media credentials from a site on the Dark Web. He now has her username and uses a clever piece of software to decipher her password. He logs into her social medial account and notices she works for ABC. A little further research reveals that ABC uses XYZ business systems.
Stage 2
With a little guesswork, the hacker uses Lily’s username (her email address!) and favourite password to log into the XYZ system!
Stage 3
He gets familiar with the software’s basic functions and sees that 47 truckloads of frozen fish will be delivered to supermarkets and wholesalers across the country in the next few days.
Stage 4
The hacker changes the temperature settings on each unit, staggering them across several hours, and removes the alert settings that would have notified Lily that something was wrong, then logs off.
Stage 5
The following days, ABC’s trucks start leaving their depots, laden with £1.6m of frozen fish. By the end of the day, with fluctuating temperatures, all 47 trucks are carrying spoiled fish. As each truckload is rejected by ABC’s customers, the scale of the crisis becomes apparent to ABC’s operations manager.
Stage 6
ABC’s customers refuse to pay for the deliveries. Some even decide to switch their order to ABC’s competitors, leaving them at a significant loss.
Stage 7
It doesn’t take ABC long to identify the cause of the problem and they narrow things down to Lily’s XYZ session. Lily is adamant she didn’t change any settings. XYZ are denying any responsibility; Lily’s credentials were correct and their system did what is was designed to do. ABC’s IT team has no idea how Lily’s credentials were compromised.
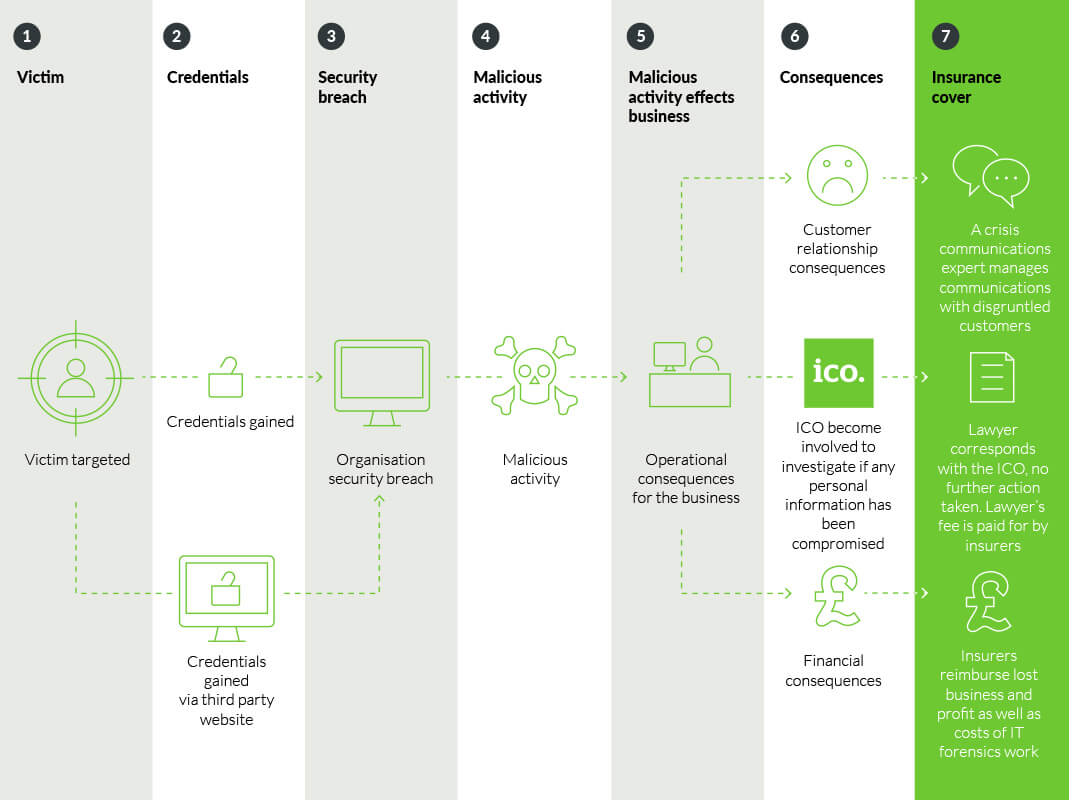
Luckily, ABC has cyber insurance.
- ABC’s cyber insurers are notified of the problem and swing into action. Insurer’s appoint an IT forensics team to investigate and they soon discover that Lily’s social media credentials, compromised in an earlier breach at the social media company, have been used by a cyber criminal to gain access to XYZ’s system.
- All user passwords are changed and access to XYZ is made subject to an additional layer of authentication (PIN numbers sent to user’s company phones).
- The cyber insurers reimburse ABC’s lost net profit following the lost consignments and subsequent lost business, as well as their unexpected additional costs. They also pay for the IT forensics work and the cost of a crisis communications expert brought in to carefully manage ABC’s communications with disgruntled customers.
- Lastly, the insurers also make a lawyer available to ABC to liaise with the Information Commissioner’s Office, who has taken an interest and wants to know if any personal information on individuals was compromised. Following some carefully worded correspondence with the ICO, the regulator decides to take not further action. The lawyer’s fee is paid for by insurers.
Other points:
The hacker isn’t with any particular cyber group. He doesn’t hold any strong political views. He just likes showing off his cyber hacking skills to ‘friends’ he knows in the hacking community. Having control of Lily’s XYZ account is a golden opportunity to show off in this way. These types of hacker are known as “Script kiddies”.
A Google survey found that at least 65% of people reuse passwords across multiple, if not all, sites. The average person reuses each password as many as 14 times. The hacker knew this.
Passwords are easy to guess. MFA (multifactor authentication) when used in conjunction with strong passwords and usernames is a highly effective way of avoiding account compromise.
